Cyberoam Next-Generation Firewalls (NGFW)
Overview
The demand of easy and all the time access to network resources has become the necessity due to workforce mobilization. Enterprises are unable to have security control over their networks because of increasing number of users for example customers, and partners who are connecting to the enterprise network from outside of the organization. Apart of it, factors like rise in number of network users, virtualization, application explosion and other etc. are resulting in loss of security control.
Here comes the Cyberoam Next-Generation Firewalls (NGFW) to solve all the security issues, it provides Layer 8 identity- based technology which offers full security control over L2-L8 and actionable intelligence to the enterprises.
Cyberoam Main Features
- Firewall
- Application Visibility & Control
- Intrusion Prevention System
- VPN (SSL VPN & IPSec)
- Web Filtering
- On-Appliance Reporting
- Bandwidth Management /QoS
- Web Application Firewall
- FleXi Ports (XP)
- IPv6 Ready
- 3G / 4G / WiMAX Connectivity
- Multiple Link Management
- Anti-Virus & Anti-Spyware
- Anti-Spam
- Outbound Spam Protection
Offers Actionable Intelligence & full control
It provides proper visibility into network and user activity and helps enterprises to have strong security control as Cyberoam’s Human Layer 8 behaves like a standard abstract layer which creates bond with real layers 2-7 in order to provide proper security control.
Equipped with Cyberoam OS
Cyberoam Next-Generation Firewalls are integrated with a sharp and efficient firmware CyberoamOS –which has tremendous next generation security features like website filtering, inline application inspection and control, Intrusion Prevention System, VPN (IPSec and SSL), HTTPS inspection, and QoS/bandwidth management. Gateway Anti-Virus, Web Application Firewall and Gateway Anti-Spam are some some of the other available features.
Provides high quality performance
The powerful hardware appliances and integrated CyberoamOS obtain the highest quality of performance from a multi-core platform and get integrated with the hardware for crypto and network acceleration.
Highly scalable
Future enhancements like security updates and security features are supported by Cyberoam’s Extensible Security Architecture. These updates and deployments can be made without changing the appliances and with minimal efforts. Moreover, for the purpose of supporting more number of users, Enterprises can add another appliance in cluster/HA.
Highly Flexible
The FleXi Port (XP) security appliances containing the FleXi Ports provide flexible network connectivity with I/O slots that provide ease of up gradation of enterprises to new technologies in the most easy and cost effective way in order to make them ready for future by allowing extra Copper/Fiber 1G/10G ports over the same security appliance.
Features Details
The Cyberoam NGFWs offer next-generation security features to organizations to protect against newly-evolving threats.
Application Visibility & Control
Cyberoam’s Visibility & control feature, having the industrial leading-coverage of 2000+ applications, allows prioritization of applications based on time, user identity, application and bandwidth providing high flexibility and real L2-L8 visibility & control. Latest application controls categorize the applications on the basis of involved risks, technology & characteristics, by providing more granular controls. The need to administrator’s manual administration to upgrade policy for new applications has be eliminated by the pro-active protection model.
Layer 8 Identity-based Security
User identity is treated by the Layer 8 technology of Cyberoam as the 8th layer or the “human layer” in the network protocol stack. This technology enables administrator to not only identify the user but control his internet activity and configure policy setting, adding speed to security etc. It crunches with Layer 2 to Layer 7 resulting in better security controls over the network. Layer-8 identity based security over AAA (service authorization, user authentication and audit with logs/reports) is offered too.
Intrusion Prevention System
Whether it’s to protect against network and application-level attacks or secure organizations by malware, DoS, DDoS, Trojans, backdoor activity, malicious code transmission and blended threats, Cyberoam Intrusion prevention system works well for securing organizations against intrusion attempts, malware, Trojan, DoS and DDoS attacks, intrusion attempts ,malicious code transmission, backdoor activity and blended threats. Cyberoam Intrusion Prevention System is there to solve all your problem efficiently.
First of its Kind On-appliance Reporting
With real time logs and reports, Cyberoam has been enjoying the status of being the only vendor in the industry to offer “On-appliance reporting”. There are 1200+ in depth reports which help to manage security, meet compliance requirement and forensic analysis, real time visibility into network and user activities etc. it also contains animated and dynamic reports, country maps and in-line graphs which make Cyberoam matchless by any network security vendor.
Virtual Private Network
In order to assure secure endpoints and network with its Threat-free Tunneling technology, Cyberoam VPN (IPsec and SSL) comes with safe remote access.
QoS Bandwidth Management
Enabling organizations to tie bandwidth policies to users, user groups, Applications, website categories, Fire wall Rules and more, Cyberoam’s Granular Layer 7 & Layer 8 bandwidth controls allow committed bandwidth to critical users at all times and also allow prioritization of business-critical application and user for bandwidth allocation, ensuring assured QoS for business critical applications like VoIP and CRM. Also it permits policies to assign idle bandwidth to other applications automatically bringing to right destination of idle bandwidth and higher ROI.
Web Filtering
Cyberoam Web Filtering provides a comprehensive database having a large number of URLs classified into 89+ categories. Cyberoam’s award winner web filtering offers blockage to harmful websites, pharming attacks, malware, phishing and undesirable content that can be resulted in direct financial losses or legal liability etc.
Web Application Firewall
Attacks like cross-site scripting (XSS), SQL injection, session hijacking, buffer overflows, URL Parameter tampering, and OWASP Top 10 web applications vulnerabilities are reduced and eliminated by an On-appliance Web Application Firewall subscription of Cyberoam protecting websites and web based applications in organizations.
Models
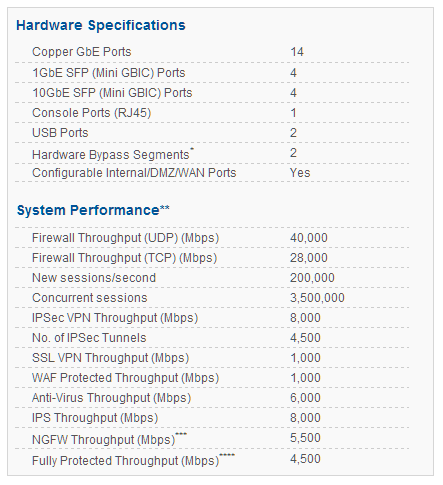
CYBEROAM CR15iNG
Cyberoam CR15iNG – Data Sheet
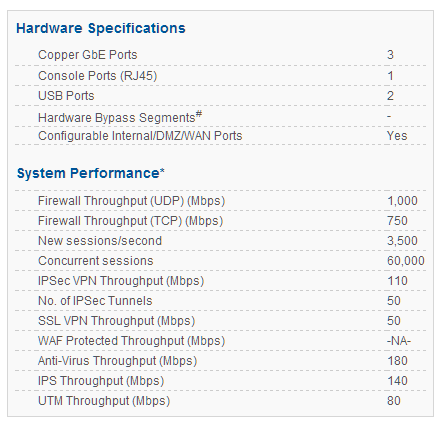
CYBEROAM CR25iNG
Cyberoam CR25iNG – Data Sheet
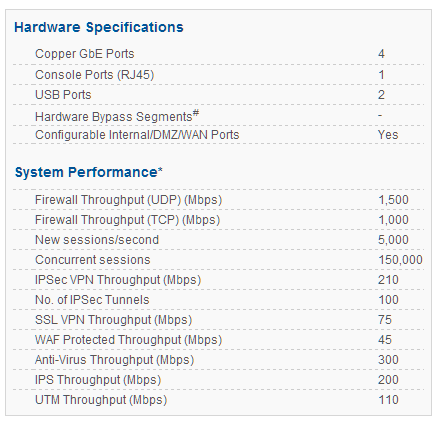
CYBEROAM CR35iNG
Cyberoam CR35iNG – Data Sheet
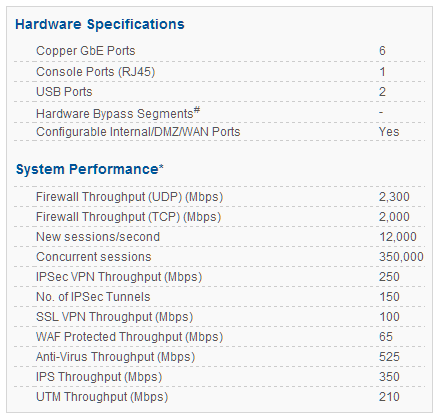
CYBEROAM CR50iNG
Cyberoam CR50iNG – Data Sheet
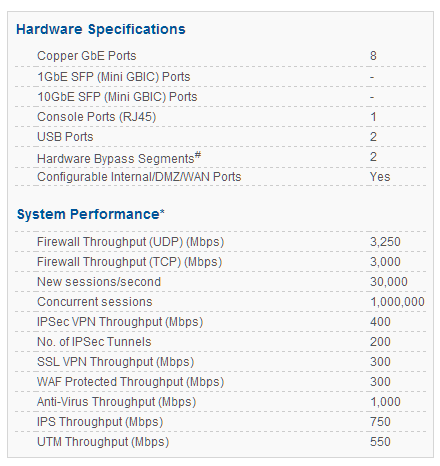
CYBEROAM CR100iNG
Cyberoam CR100iNG – Data Sheet
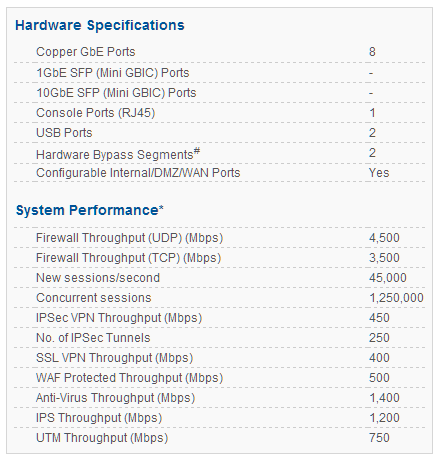
CYBEROAM CR200iNG
Cyberoam CR200iNG – Data Sheet
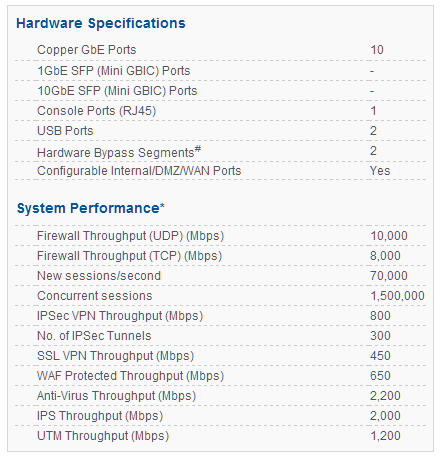
CYBEROAM CR200iNG-XP
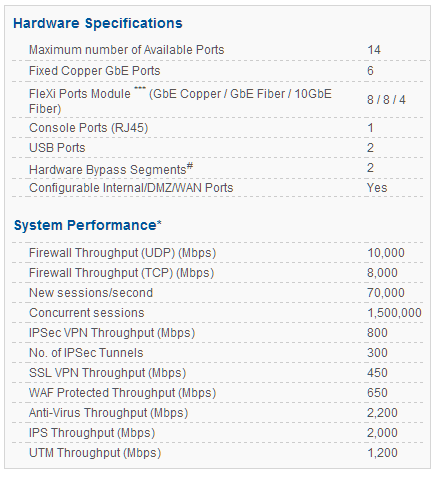
CYBEROAM CR300iNG
Cyberoam CR200iNG -XP – Data Sheet
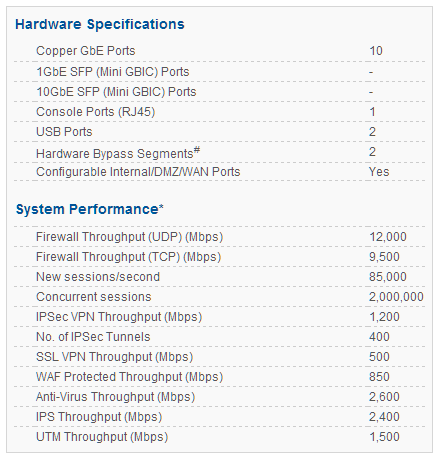
CYBEROAM CR300iNG-XP
Cyberoam CR300iNG -XP – Data Sheet
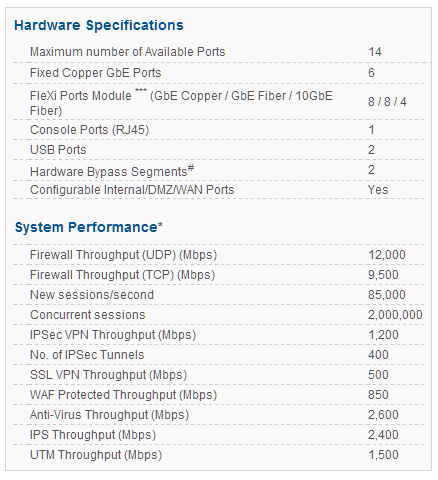
CYBEROAM CR500iNG-XP
Cyberoam CR500iNG -XP – Data Sheet
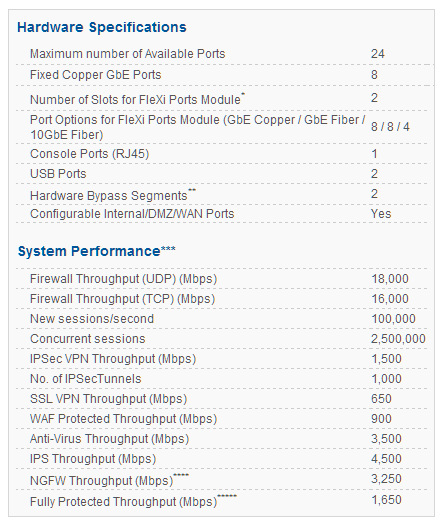
CYBEROAM CR750iNG-XP
Cyberoam CR750iNG -XP – Data Sheet
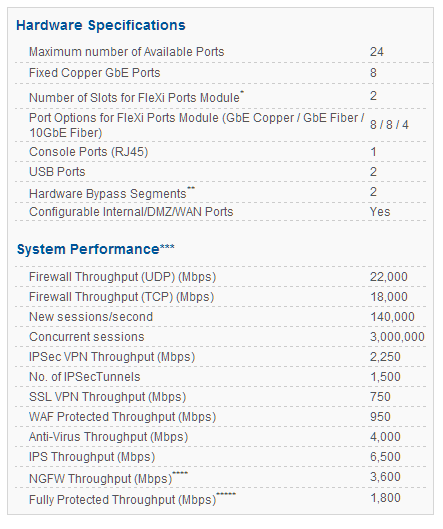
CYBEROAM CR2500iNG
Cyberoam CR2500iNG -XP – Data Sheet